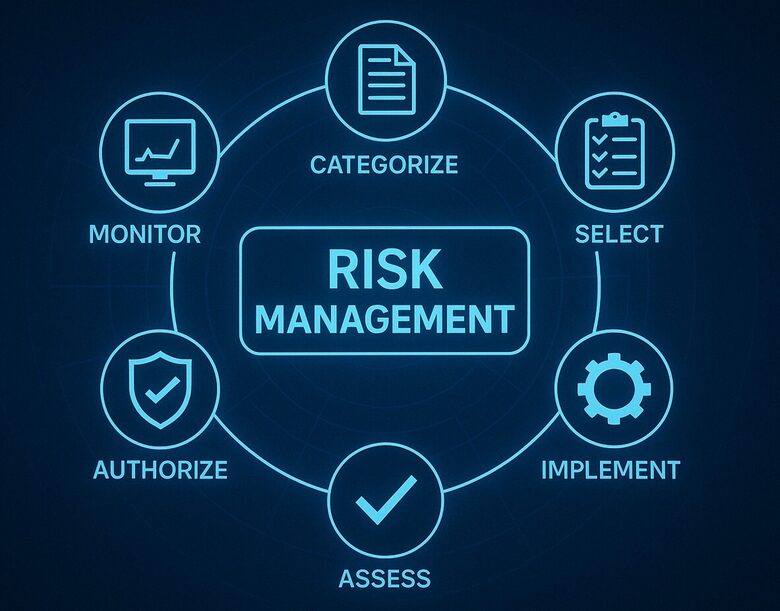
Cybersecurity Services
As a cybersecurity professional, I provide high-impact services designed to help organizations protect their digital assets, manage cyber risks, and respond effectively to security incidents. My approach combines strategic vision with technical expertise, ensuring tailored solutions that align with your business objectives.